
The newest P-Sequence PBX firmware comes with a set of updates that make your system safer, compliant, and simpler to handle.
Most notably, it delivers built-in STIR/SHAKEN help to assist service suppliers meet FCC and CRTC necessities and guarantee trusted communications. Alongside that, it provides Purple Hat SSO Integration to simplified consumer administration and allow seamless single sign-on. Lastly, it permits to choose and monitor DOD instantly through BLF.
👉 Learn on to discover what’s new, why it issues, and tips on how to get began with these new options!
Leap to ↓
- New Options
- Associated Assets →
- New Characteristic Configuration Guides
- Extra Supported SSO Integrations (Microsoft, Google)
- P-Sequence PBX Updates from the Previous 12 months
- PBX Firmware Updates and Free Trial
New Options
Constructed-in STIR/SHAKEN Soution
STIR/SHAKEN is a set of protocols and frameworks designed to fight caller ID spoofing on public phone networkst. The FCC within the U.S. and the CRTC in Canada have required carriers to undertake these protocols since 2021.
We’re very excited to announce that the P-Sequence PBX Cloud Version helps built-in STIR/SHAKEN implementation for shared trunks now!
This implies no want for exterior signing providers, third-iparty SBCs, handbook set up, or further prices, permitting you to leverage the industry-standard name authentication framework instantly inside your telephone system.
Constructing the STIR/SHAKEN framework natively into the PBX is a key step that will help you meet world telecom regulatory necessities simply; cut back spoofing, fraud, and robocalls effectively; and increase buyer belief and satisfaction successfully.
Key Capabilities of STIR/SHAKEN in Yeastar PBX
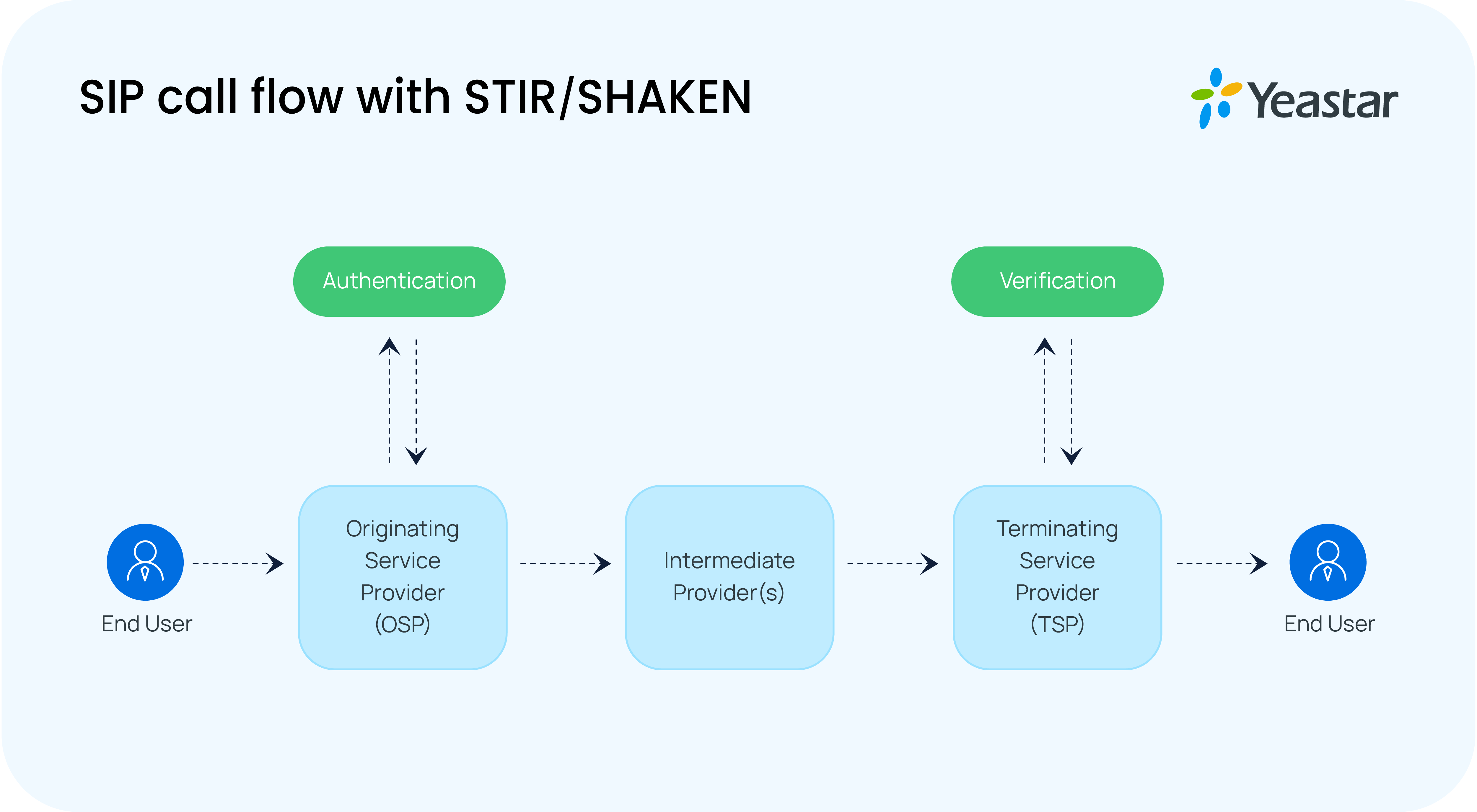
With the built-in STIR/SHAKEN help, the system affords a whole framework for name athentication and verification.
- Outbound name signing: Mechanically indicators outbound calls on the uploaded digital certificates, excluding emergency numbers or expired certificates.
- Inbound name verification: Retrieves the general public key and validates the signature to confirm incoming calls.
- Name filtering: Drop the untrusted or unsafe calls, together with these from upstream carriers.
- Verification end result logging: Information all verification ends in CDRs for straightforward overview and traceability.

Configure STIR/SHAKEN on YCM
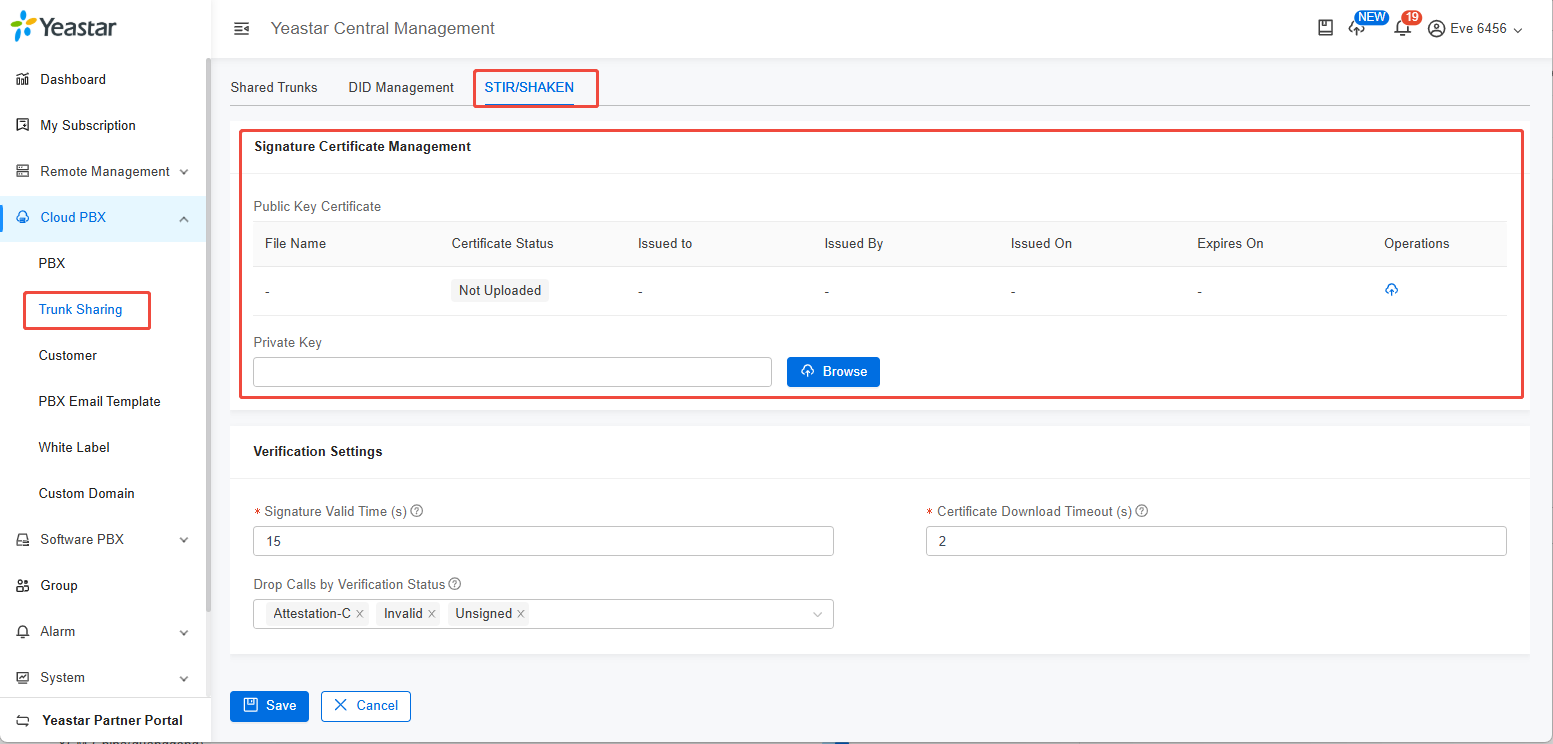
Earlier than continuing with the service implementation, please word that it’s necessary for each associate to acquire the SS certificates from the coverage administrator. Find out how to acquire the STI certificates, discover on this weblog. Then full the setup on the Yeastar Central Administration (YCM) platform with this course of:
- Log in to YCM, navigate to Cloud PBX → Trunk Sharing, and observe the on-screen directions to start out the setup.
- Add the certificates and personal key, used for signing outbound calls to authenticate caller identification.
- Set verification technique, configure how inbound calls are verified and dealt with, together with signature legitimate time, certificates obtain timeout and drop calls with verification standing.
- Allow STIR/SHAKEN on shared trunks, with versatile choices to use signing, verification, each, or disable totally, supporting dealing with of calls from upstream carriers.
For detailed setup directions, please seek advice from the configuration information.
*Notice: To make use of this function, be sure each your PBX and YCM are up to date to the most recent variations. STIR/SHAKEN is already obtainable on the most recent PCE (Yeastar Hosted). Help for PCE (BYOI) will go reside on November 17.

Purple Hat SSO Integration
This time, the PBX provides help for an additional SSO integration device — Purple Hat.
Earlier than diving into the function itself, let’s take a fast have a look at Purple Hat and its Single Signal-On (SSO) resolution.
About Purple Hat:
Purple Hat, Inc. is an American software program firm recognized for its open-source enterprise options. Its flagship product, Purple Hat Enterprise Linux (RHEL), is broadly utilized by companies to construct and handle safe, scalable IT environments.
About Purple Hat Single Signal-On (SSO)
Purple Hat SSO offers a unified login resolution for internet purposes and RESTful internet providers. It allows customers to entry a number of techniques with one set of credentials whereas giving directors centralized management over authentication and safety insurance policies.
The way it works with P-Sequence PBX
Constructed on the SAML 2.0 protocol, the P-Sequence PBX can now combine seamlessly with Purple Hat SSO, with the PBX appearing because the Service Supplier (SP) and Purple Hat because the Id Supplier (IdP).
This enables the PBX, through the SSO course of, to provoke an authentication request, whereas Purple Hat is accountable for verifying the consumer’s identification and issuing authentication credentials.
Key Capabilities
This integration enhances each compatibility and safety whereas automating consumer administration:
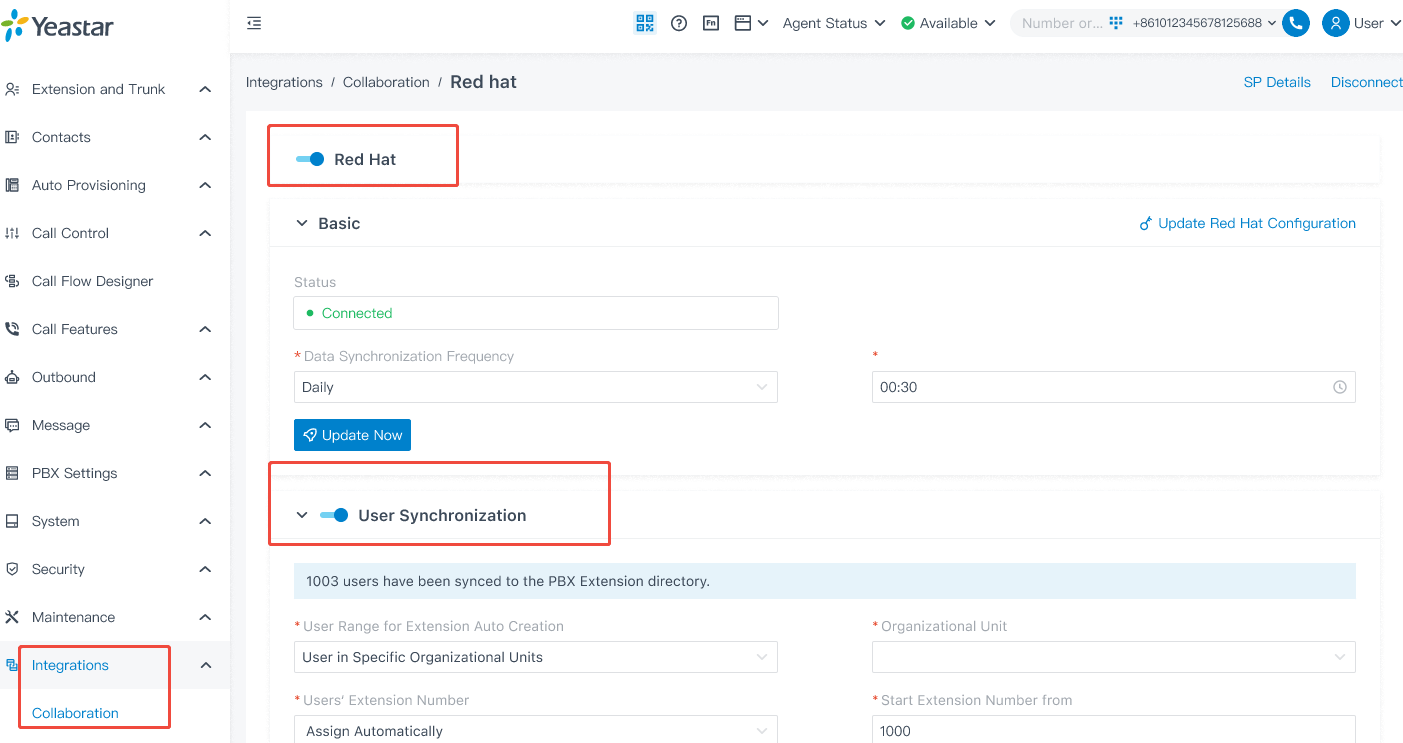
- Auto consumer sync and extension creation: Sync Purple Hat customers in particular organizations or teams robotically and create extensions based mostly on predefined guidelines.
- Delete the Extensions not in sync: Take away extensions when customers are not synced (admin-configurable).
- Person info synchronization: Maintain profile particulars akin to title, electronic mail, telephone quantity, and job title at all times updated.
- Single sign-on (SSO): Allow customers to log in to the PBX, together with the Linkus Desktop and Net Purchasers, instantly with their Purple Hat account, with out repeated logins or further passwords.
This integration simplifies account administration for admins by eliminating repetitive operations and platform switching, whereas giving customers a seamless, safe one-click login expertise.
*Study extra about this integration and tips on how to set it up on the function web page or configuration information.

Change DOD through BLFs
The P-Sequence PBX now helps setting DOD through function code. Customers can simply choose their outbound quantity by getting into the function code + DOD instantly from the telephone interface, or selecting it on the Linkus UC Purchasers panel. In the meantime, admins can monitor monitor DOD switching via BLF for improved visibility and management.
This permits customers to show completely different firm numbers for various shoppers and provides admins clear oversight of trunk utilization.

Further Optimizations
SIP 302 Redirect Help: To fulfill French regulatory necessities, P-Sequence PBX now helps SIP 302 Redirect. When a name is forwarded to an exterior quantity, the unique caller ID is preserved, permitting the recipient to see who’s really calling.
For extra particulars about this P-Sequence replace, go to the discharge notes right here: Cloud Version | Equipment Version | Software program Version
Newly Supported Telephone Fashions (Oct 15 – Nov 11)
| Vendor | Telephone Mannequin |
|---|---|
| Snom | E303, SnomD892, SnomD895 |
Verify the auto-provision help listing for 500+ IP telephones.
Associated Assets
New Characteristic Configuration Guides
Step-by-step directions for:
Extra SSO Integration platforms
P-Sequence PBX additionally helps three fashionable SSO platforms to simplify consumer authentication and administration. Discover the main points 👇
Sustain with the most recent P-Sequence Updates
- Omnichannel Message API, PBX API Bulk Entry and Extra (Oct 2025)
- AI Name Transcription & Abstract, Digital Fax & Extra (Sep 2025)
- Outbound Bulk Messaging, Group Reply for Queues, Name Compliance & Extra (Aug 2025)
- Name Stream Designer, Textual content-to-Speech, Voicemail Transcription, and Extra (July 2025)
- Presence Customization, Linkus CarPlay, S-Sequence to P-Sequence Migration, and Extra (June 2025)
- Dynamics 365 CRM Integration, Google SSO Integration, and Extra (Could 2025)
- CRM Integration Template, Name Notice, and Extra (March 2025)
- Outbound Name Heart, Multi-Time Zone, and Extra (February 2025)
- Resort Administration, Unreturned Missed Name Report, and Extra (January 2025)
- Quantity Masking, NEC IP Telephone Auto Provisioning, and Extra (December 2024)
- Prolonged YCM Activity Help, PSE White Label, and Extra (November 2024)
Improve Your PBX and Begin a Free Trial
- For PBX Admins: Improve your firmware via the administration portal to discover the most recent options.
- For New Customers: Begin a 30-day free trial and uncover your favourite options.


